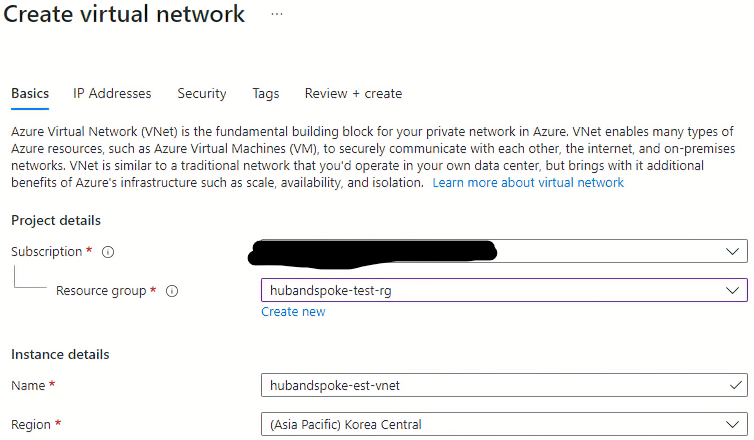
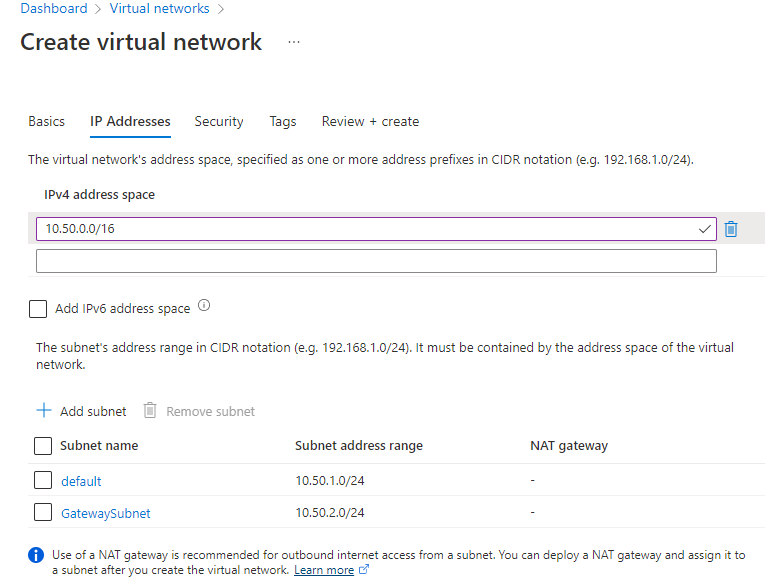
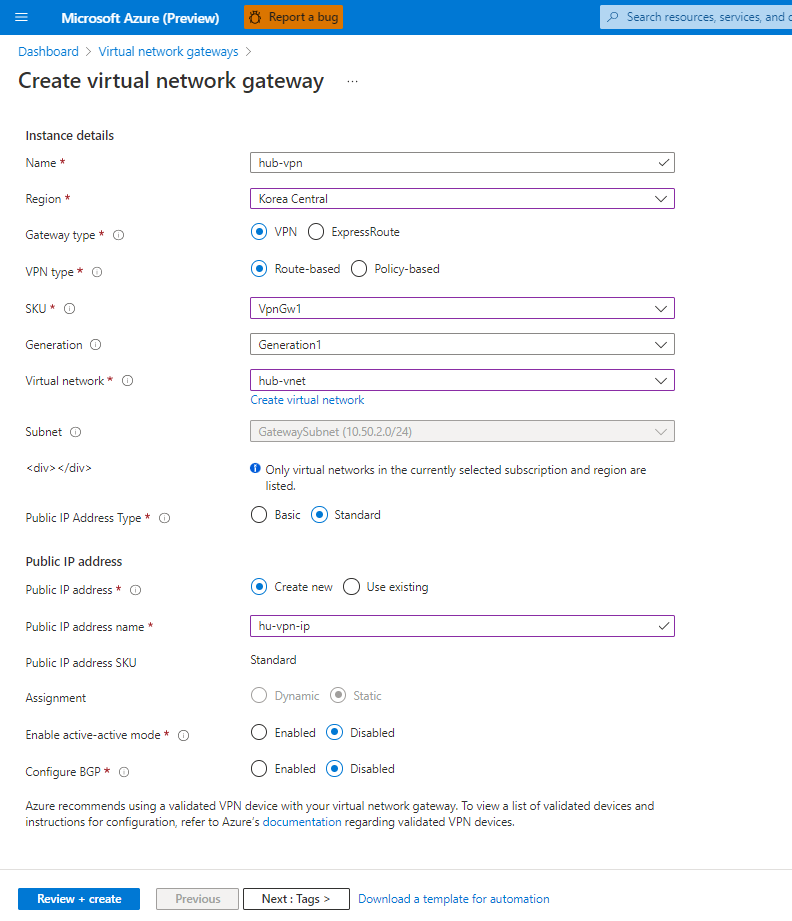
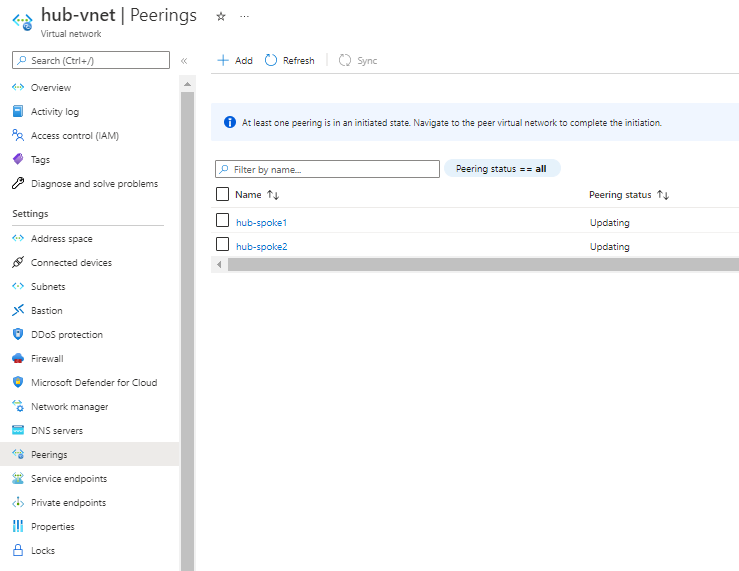
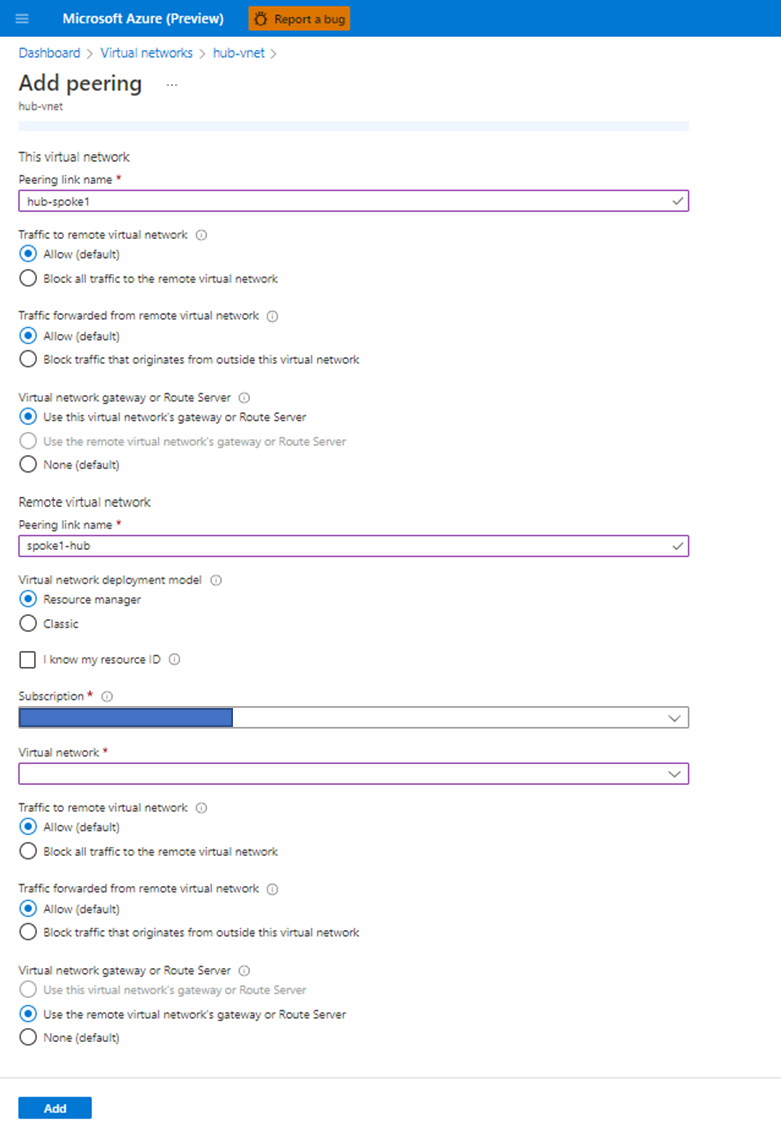
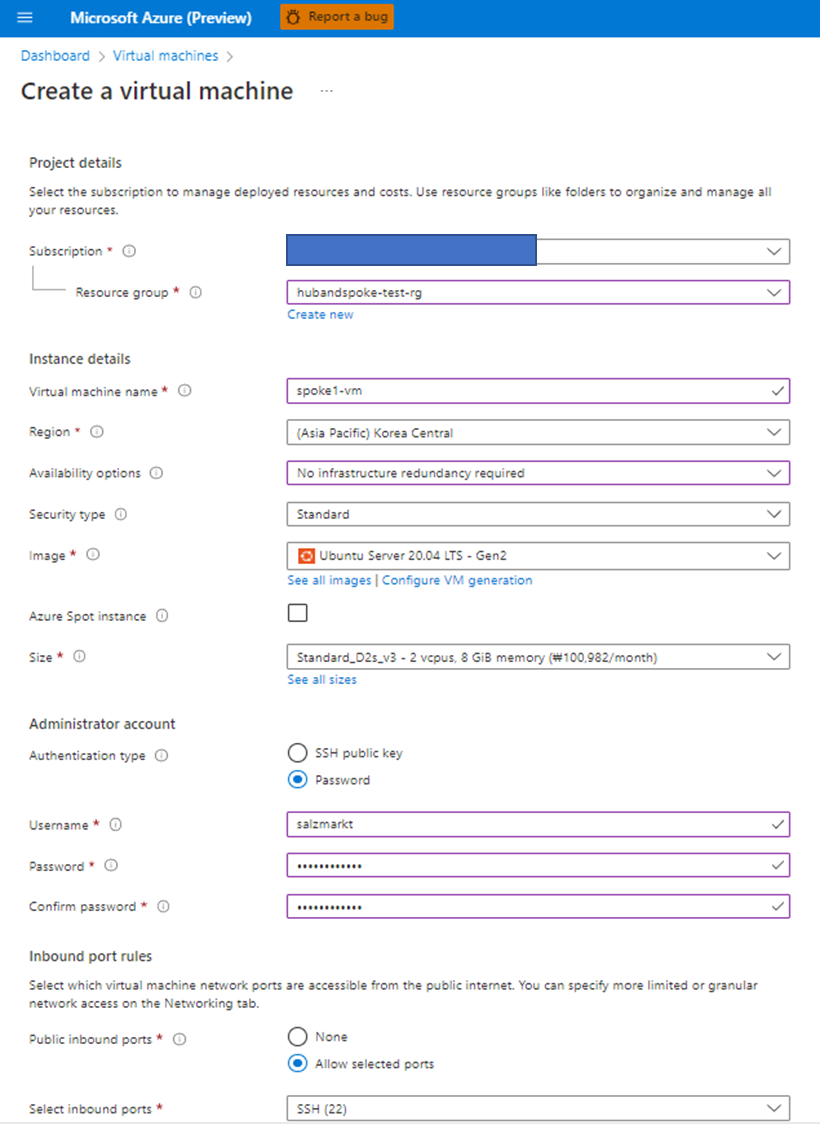
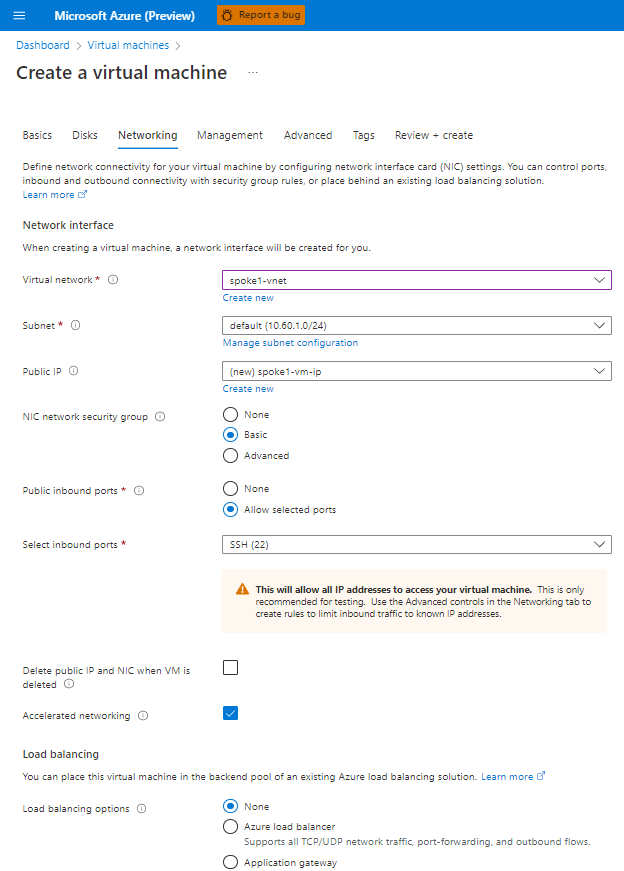
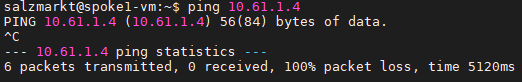
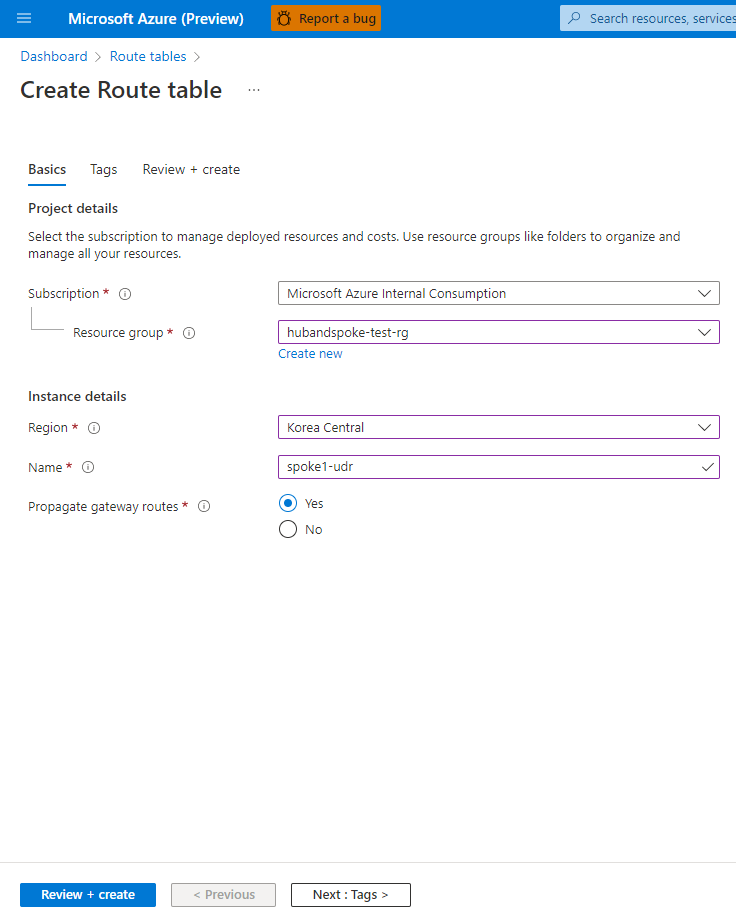
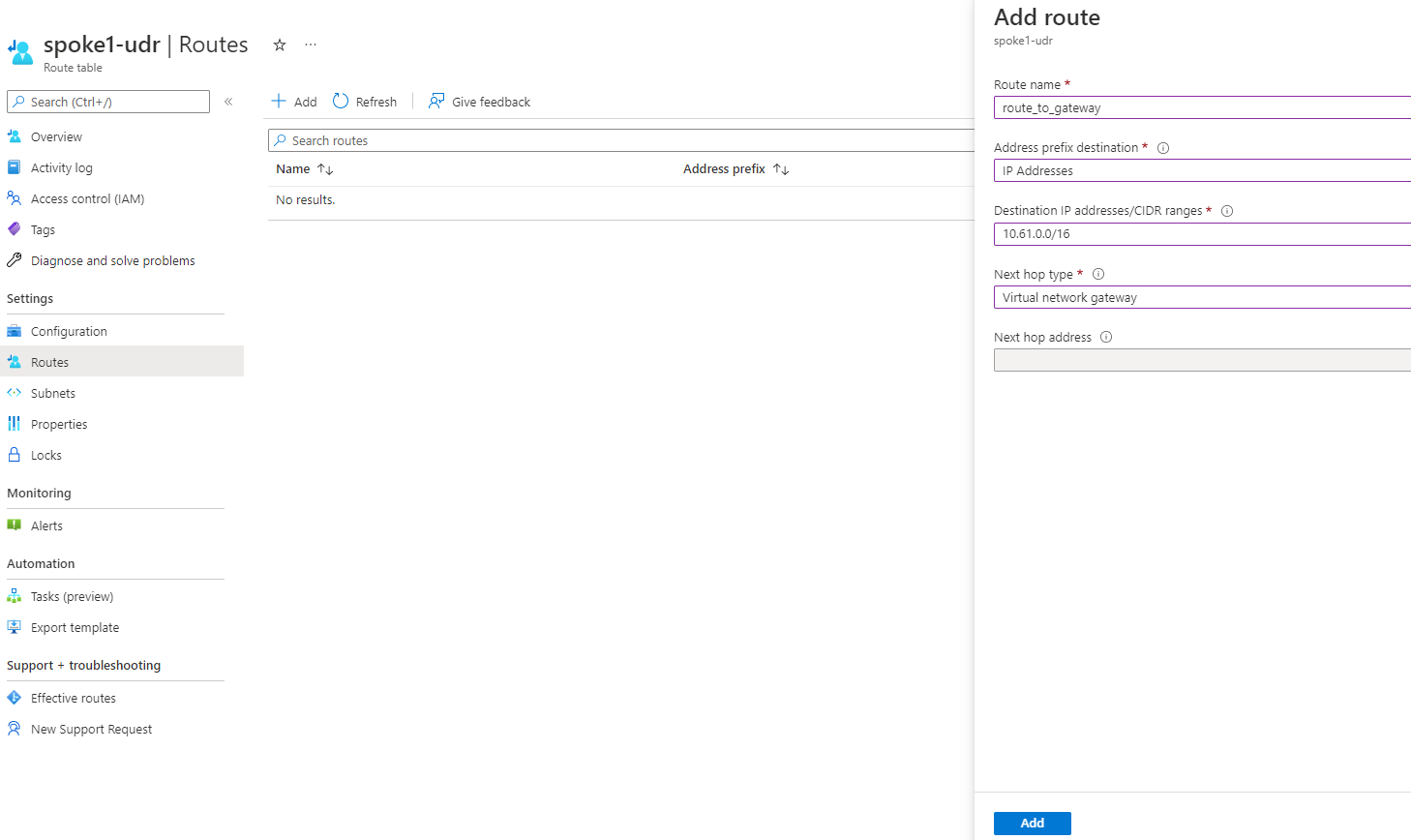
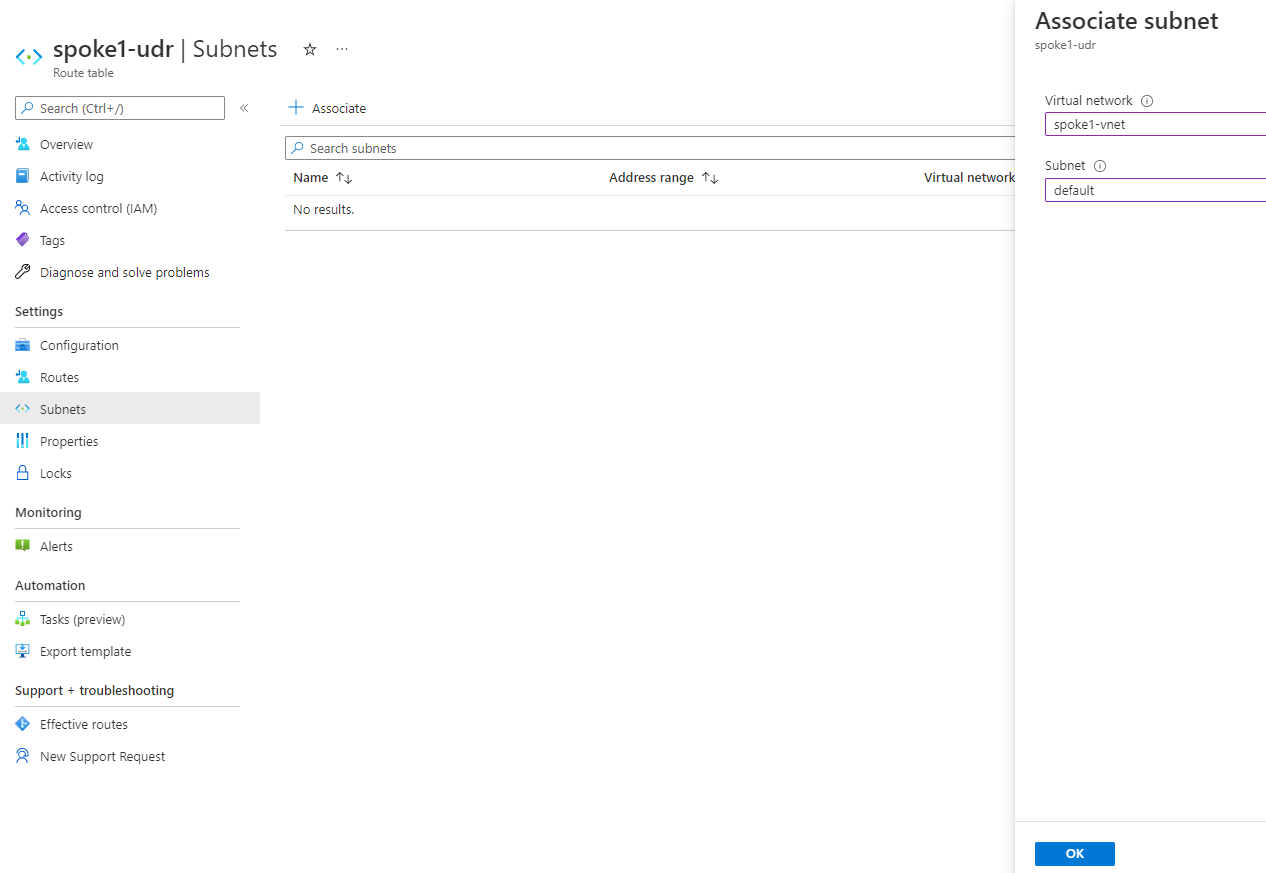
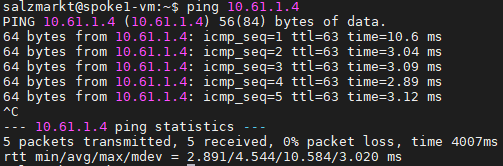
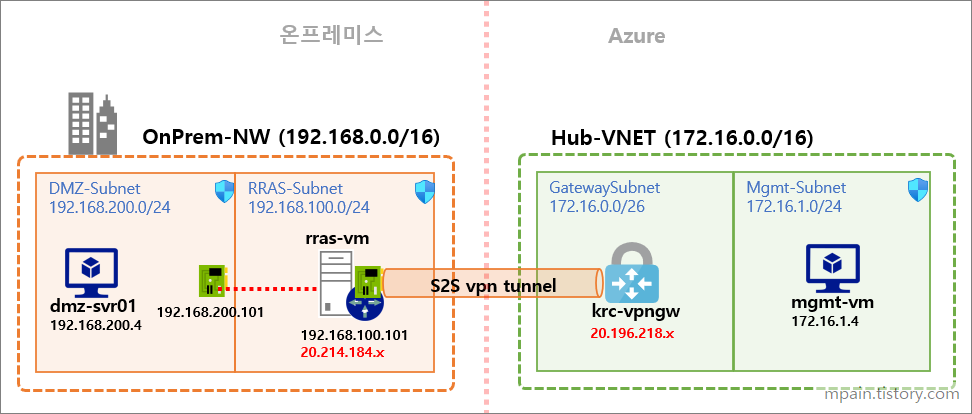
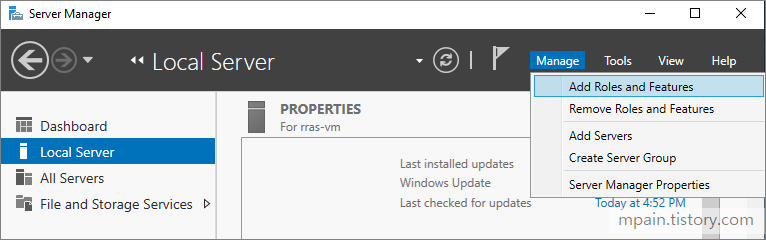
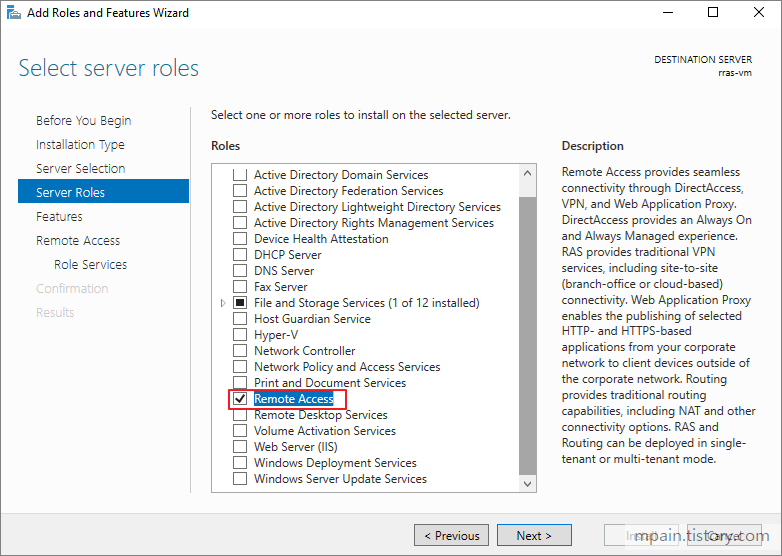
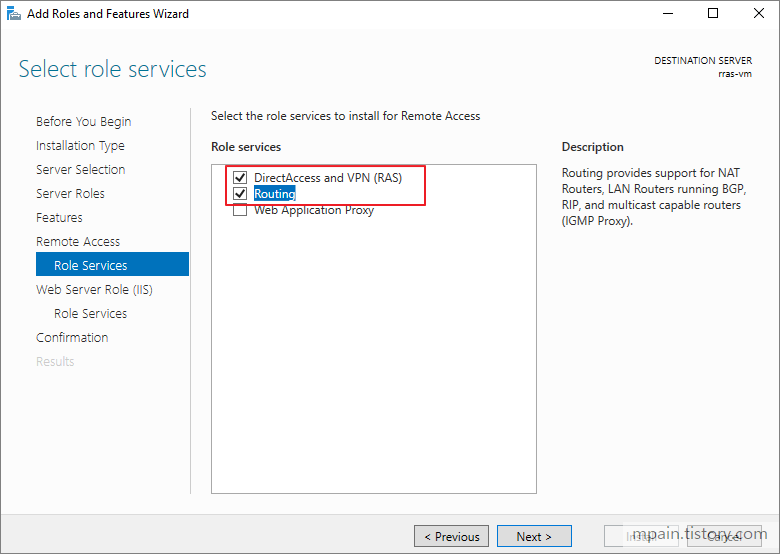
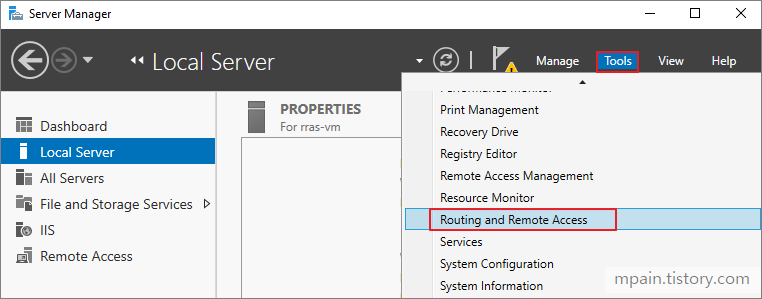
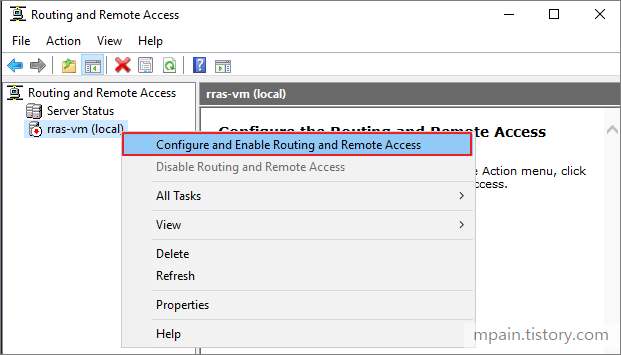
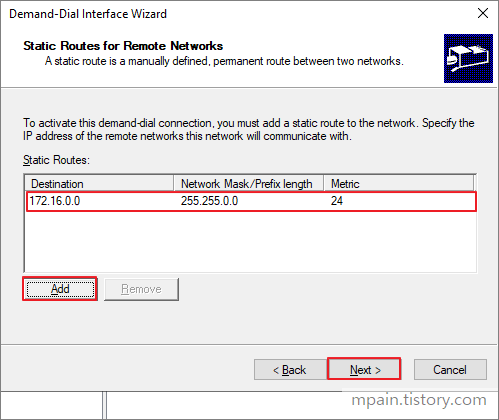
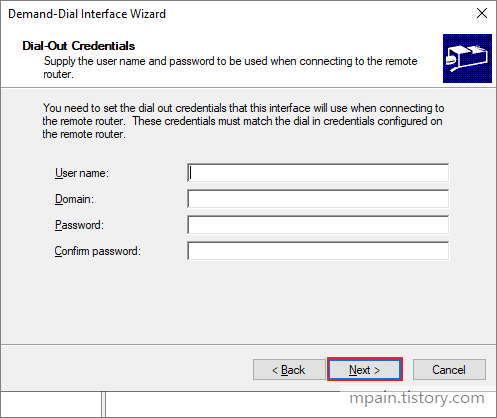
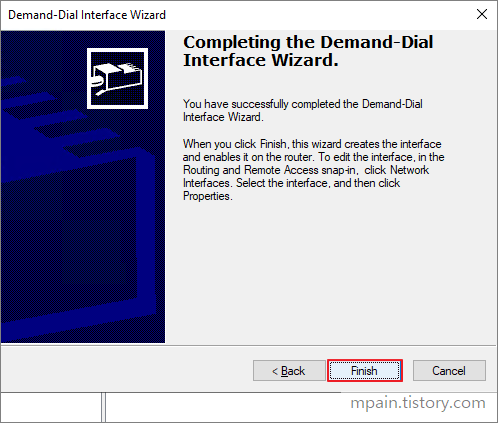
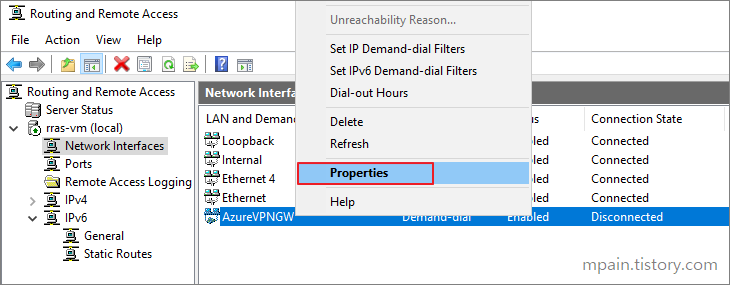
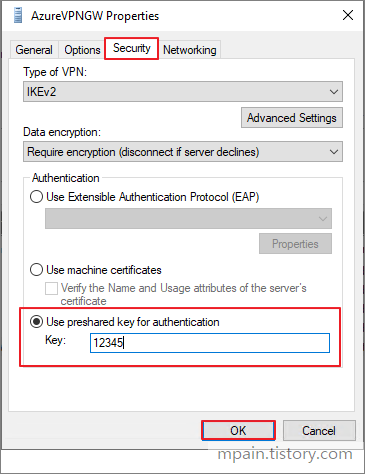
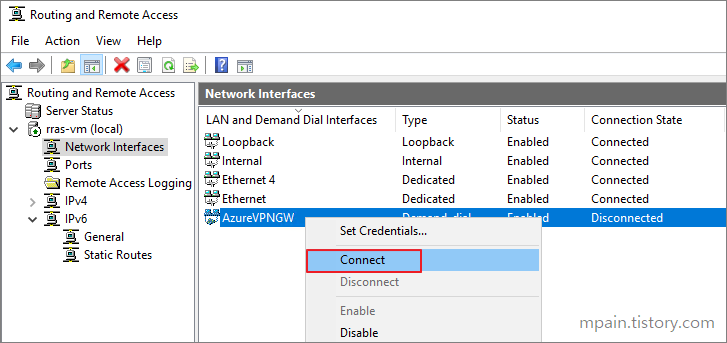
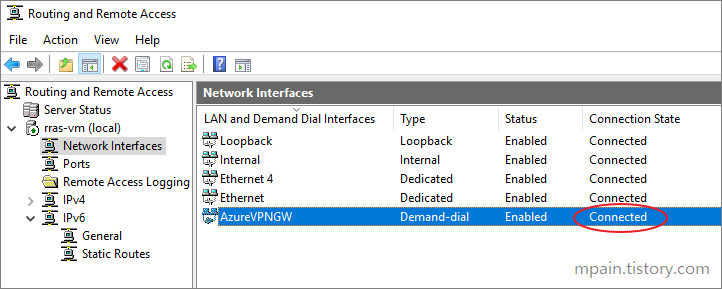
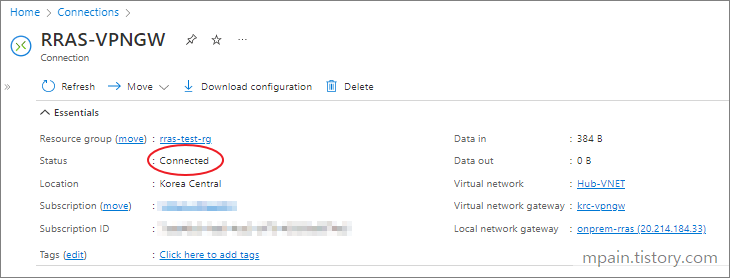
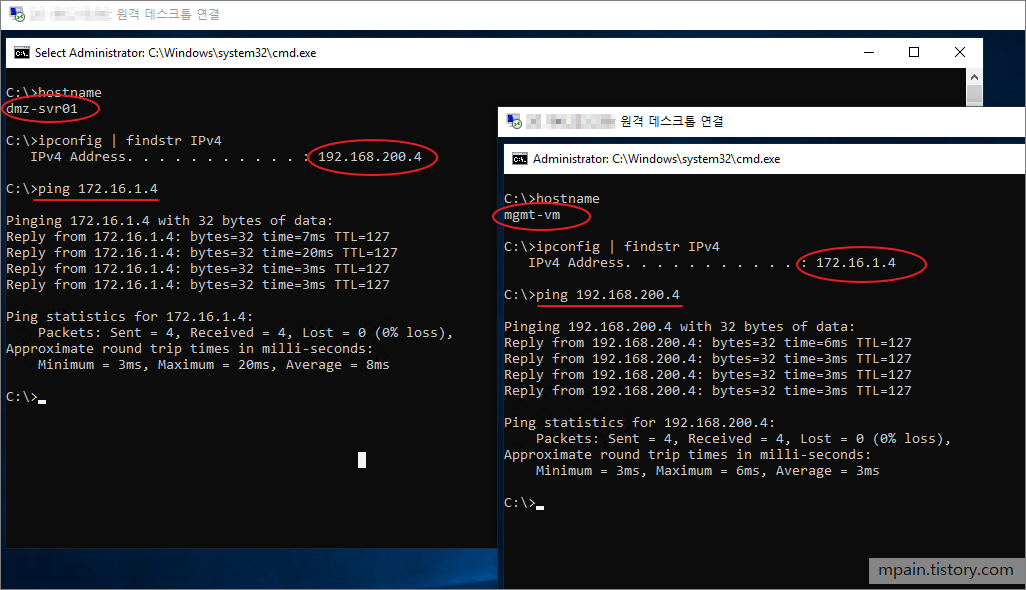
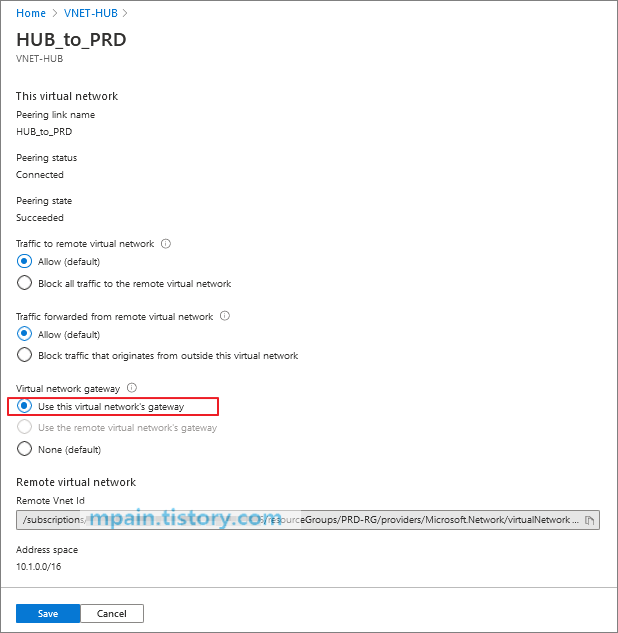
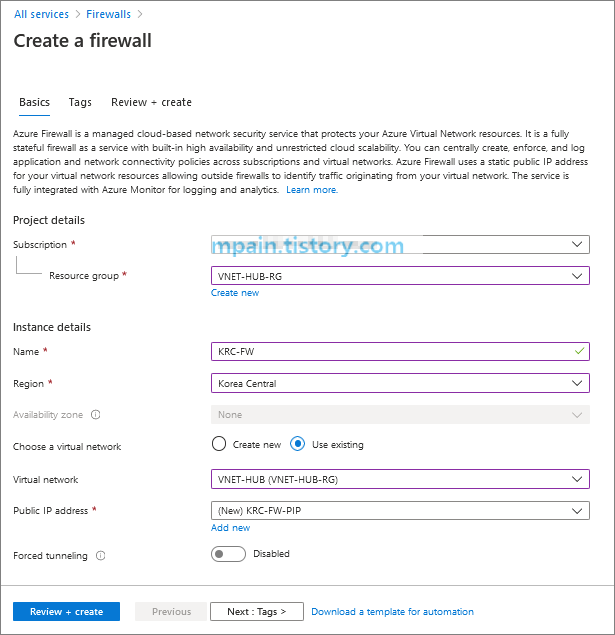
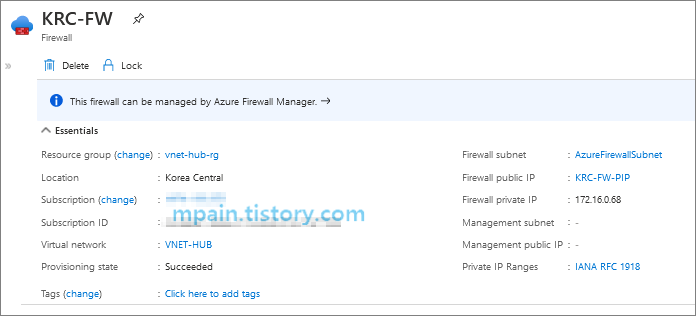
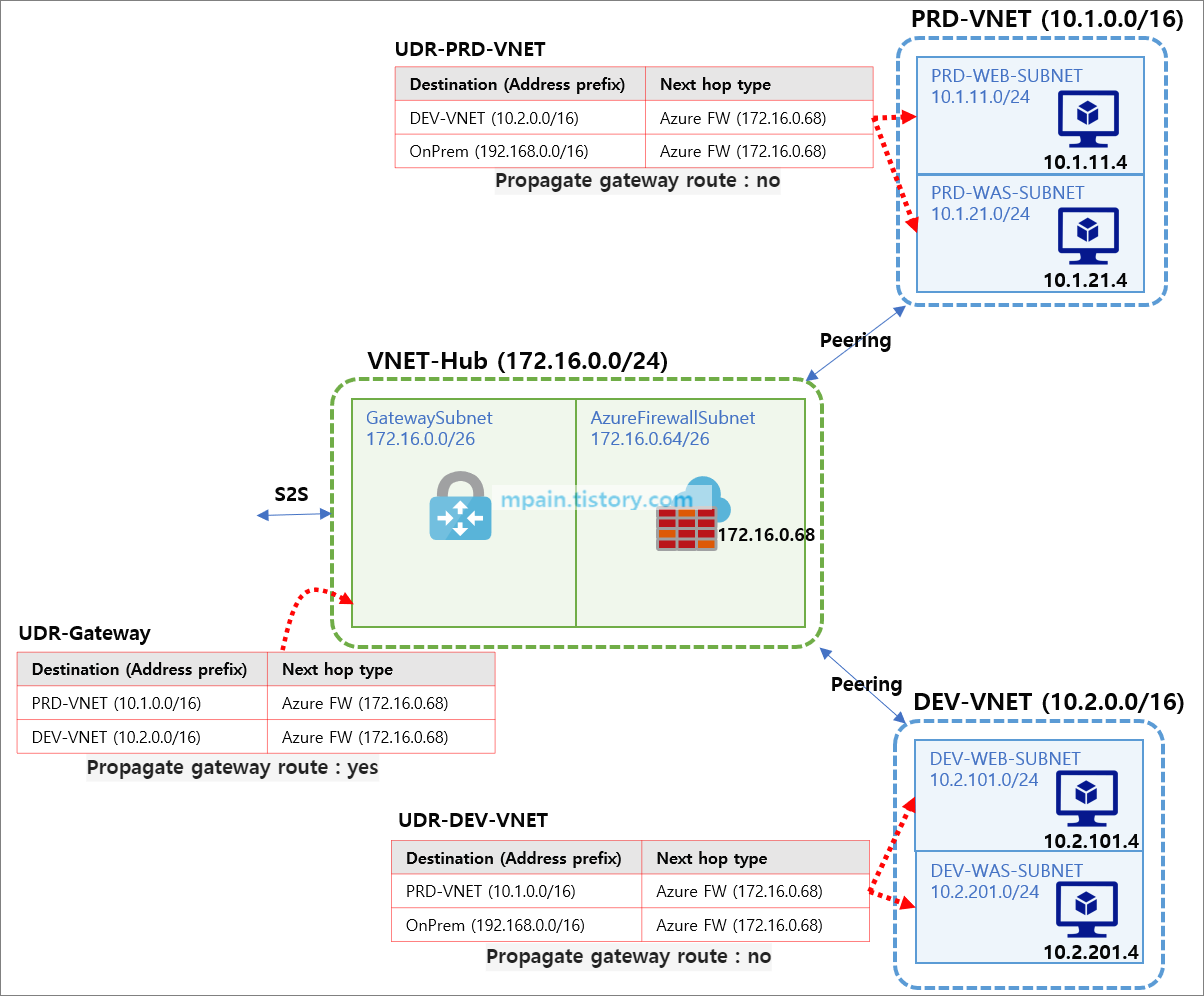
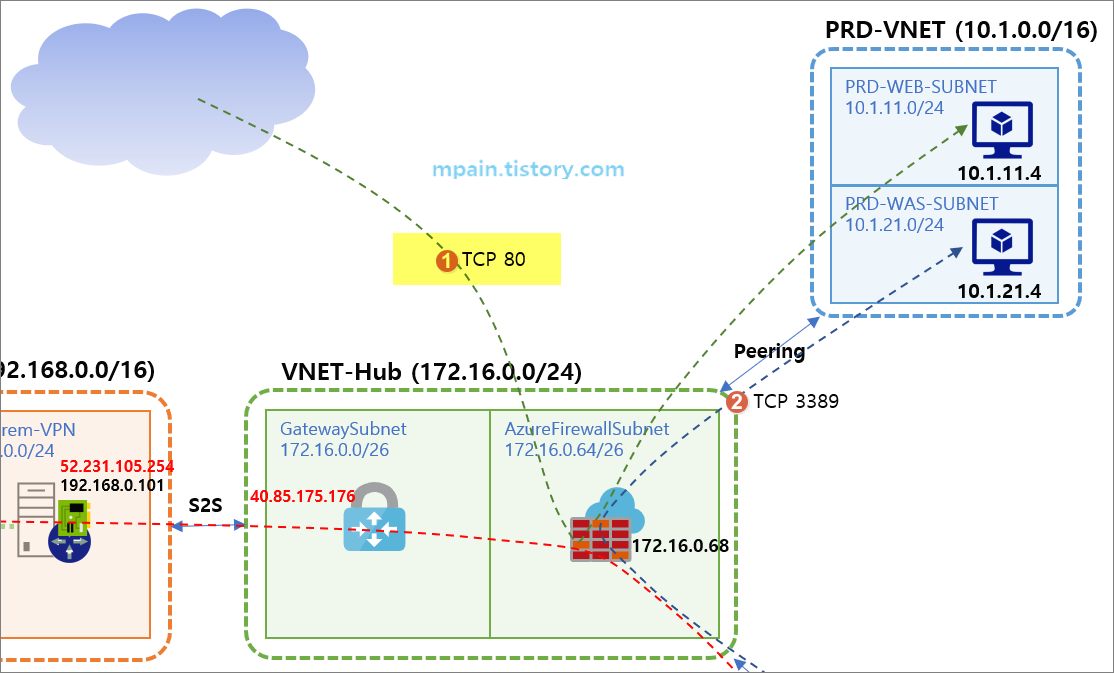
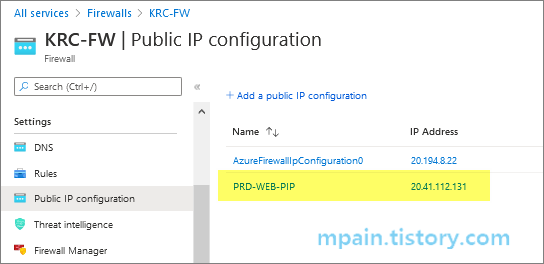
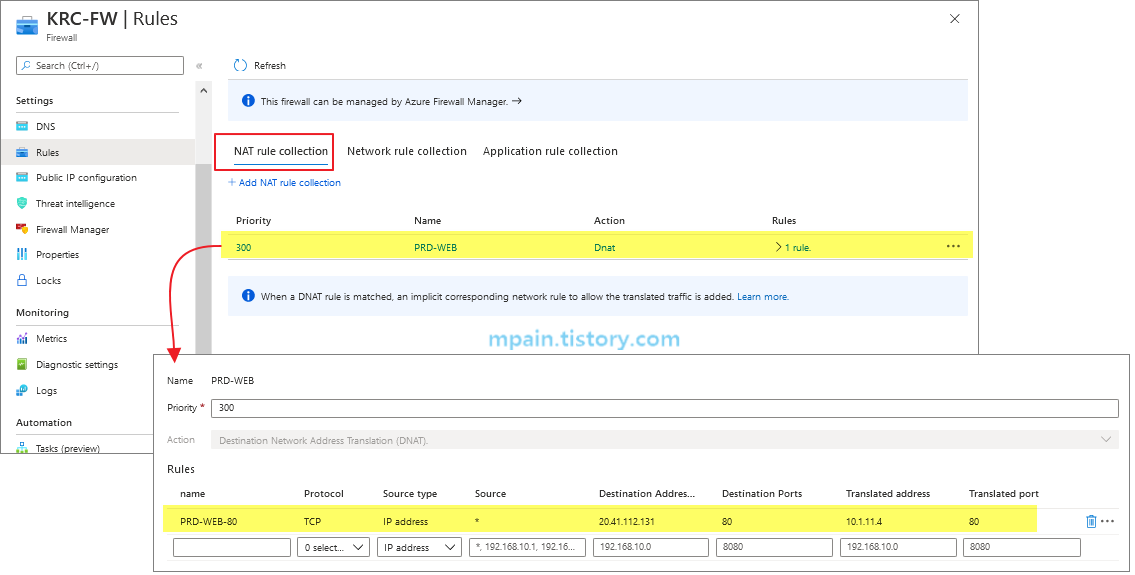
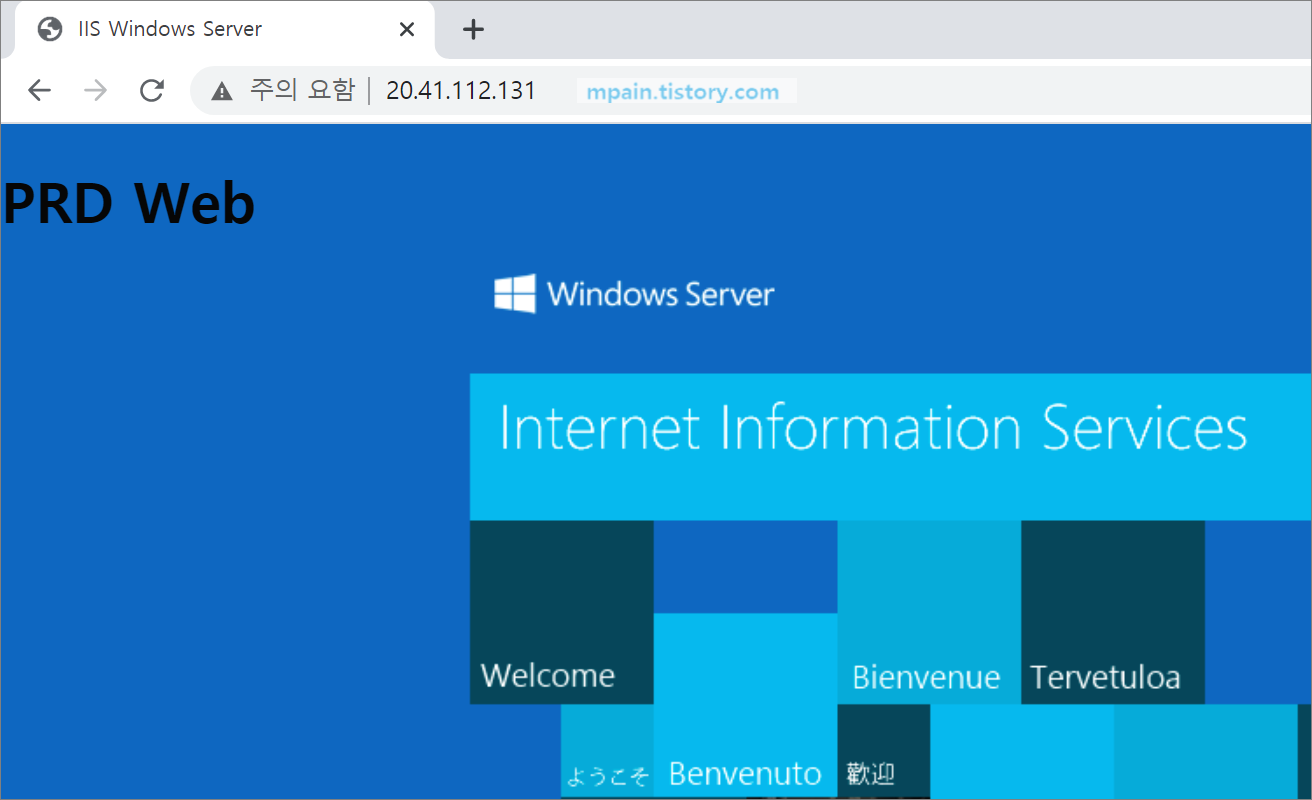
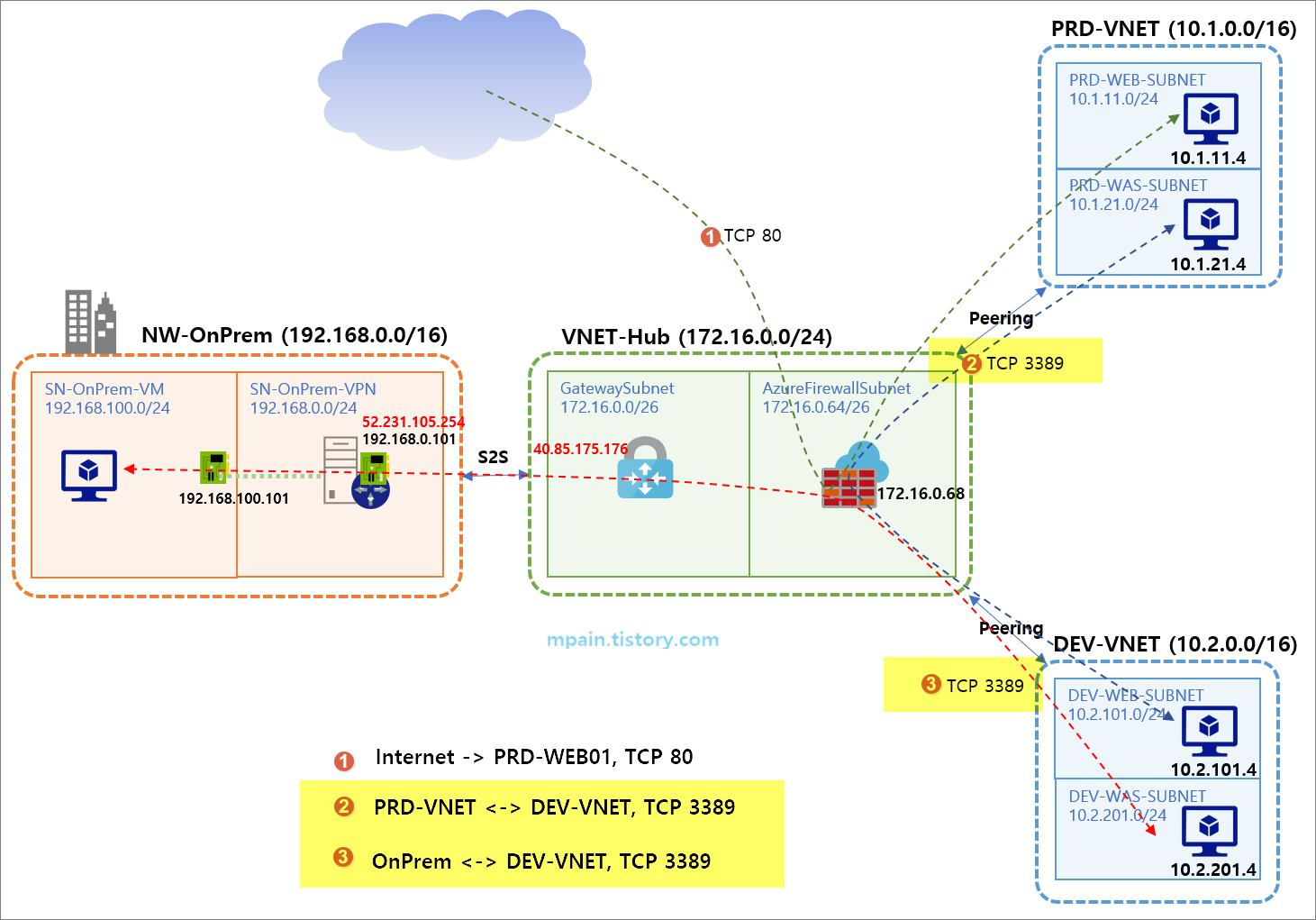
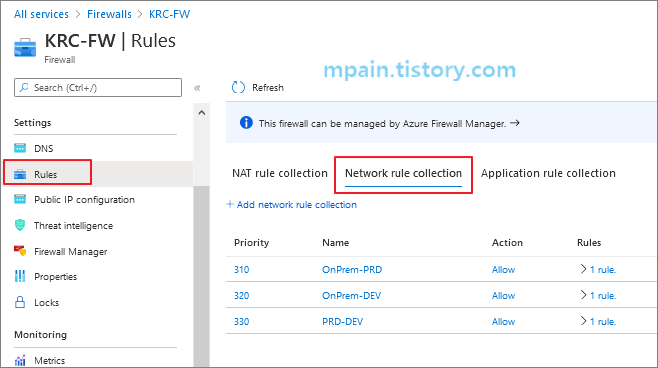
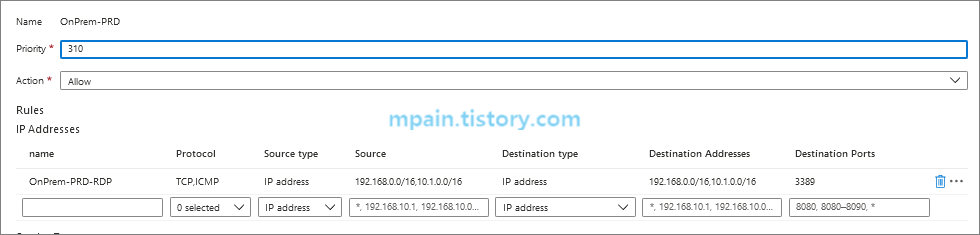
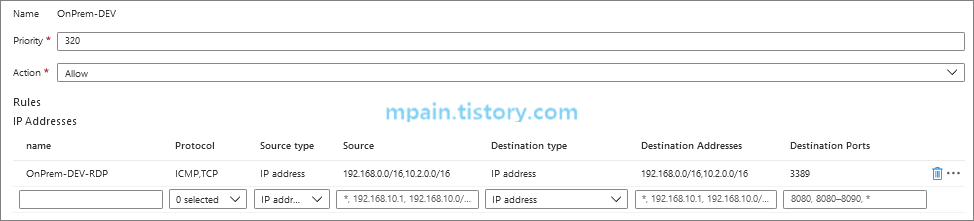
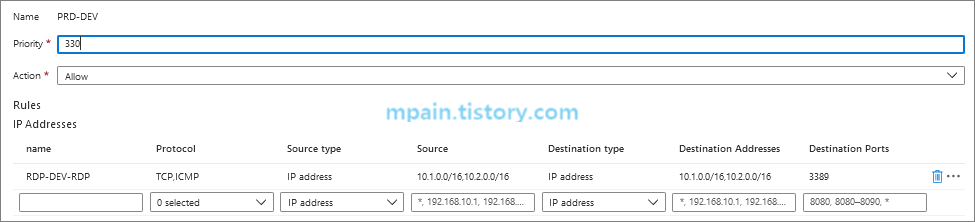
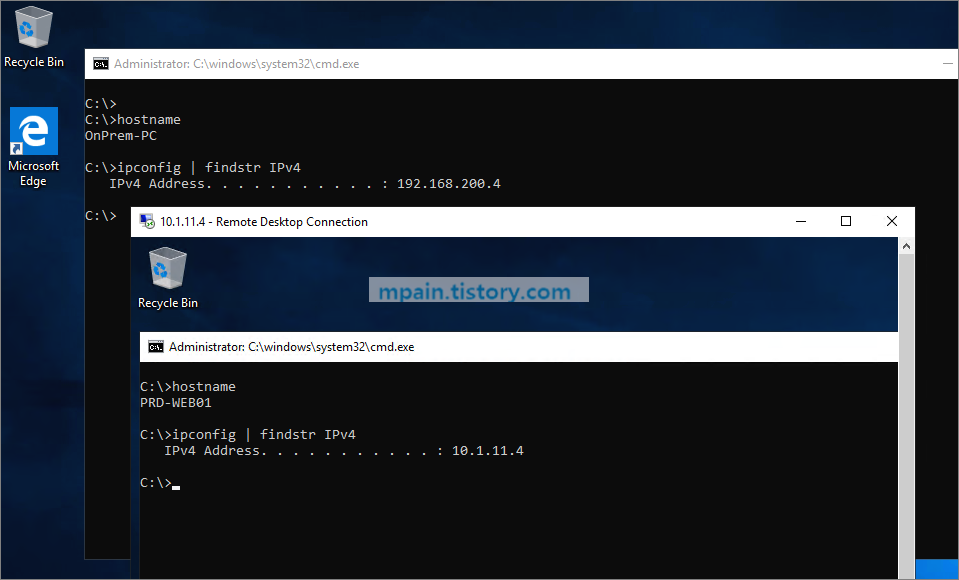
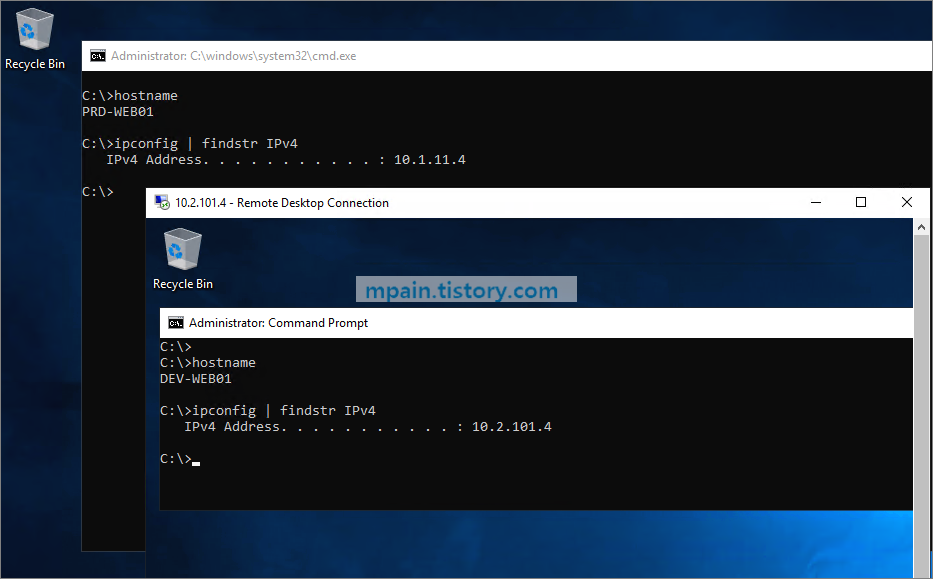
Azure Private Link를 사용하면 가상 네트워크의 프라이빗 엔드포인트를 통해 Azure PaaS Services(예: Azure Storage 및 SQL Database)와 Azure 호스팅 고객 소유/파트너 서비스에 액세스할 수 있습니다.
가상 네트워크와 서비스 사이의 트래픽은 Microsoft 백본 네트워크를 통해 이동합니다. 서비스를 공용 인터넷에 더 이상 노출할 필요가 없습니다. 가상 네트워크에 자체 프라이빗 링크 서비스를 만들어서 고객에게 제공할 수도 있습니다. Azure Private Link를 사용한 설치 및 소비는 Azure PaaS, 고객 소유 및 공유 파트너 서비스에서 일관적입니다.
중요
Azure Private Link가 이제 일반 공급됩니다. 프라이빗 엔드포인트 및 Private Link 서비스(표준 부하 분산 장치 뒤의 서비스)가 모두 일반 공급됩니다. 다른 Azure PaaS는 다른 일정에 따라 Azure Private Link에 온보딩됩니다. Private Link에서 Azure PaaS의 정확한 상태는 Private Link 가용성을 참조하세요. 알려진 제한은 프라이빗 엔드포인트 및 Private Link Service를 참조하세요.
주요 이점
Azure Private Link는 다음과 같은 이점이 있습니다.
- Azure 플랫폼의 프라이빗 액세스 서비스: 프라이빗 엔드포인트를 사용하여 가상 네트워크를 Azure에서 애플리케이션 구성 요소로 사용할 수 있는 모든 서비스에 연결합니다. 서비스 공급자는 자체 가상 네트워크에서 서비스를 렌더링할 수 있으며, 소비자는 로컬 가상 네트워크에서 이러한 서비스에 액세스할 수 있습니다. Private Link 플랫폼은 Azure 백본 네트워크를 통해 소비자와 서비스 간의 연결을 처리합니다.
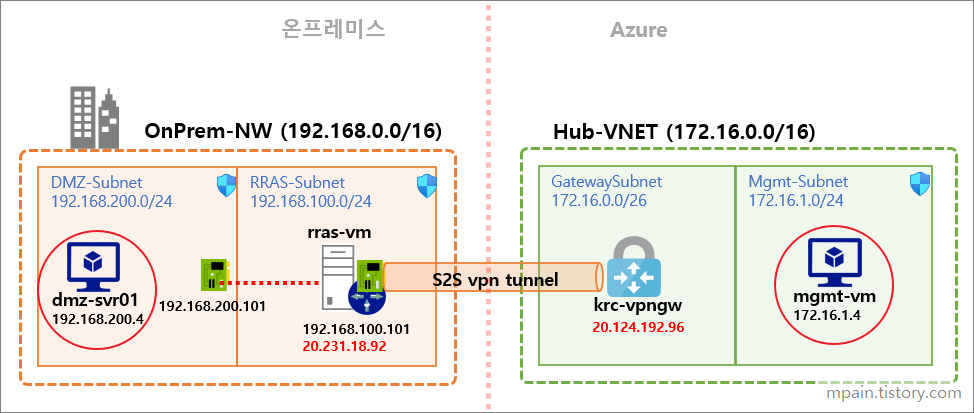
- 온-프레미스 및 피어링된 네트워크: 프라이빗 엔드포인트를 사용하여 온-프레미스에서 ExpressRoute 개인 피어링, VPN 터널 및 피어링된 가상 네트워크를 통해 Azure에서 실행되는 서비스에 액세스할 수 있습니다. 서비스에 연결하기 위해 ExpressRoute Microsoft 피어링을 구성하거나 인터넷을 트래버스할 필요가 없습니다. Private Link는 워크로드를 Azure로 안전하게 마이그레이션하는 방법을 제공합니다.
- 데이터 유출 방지: 프라이빗 엔드포인트는 전체 서비스가 아닌 PaaS 리소스의 인스턴스에 매핑됩니다. 소비자는 특정 리소스에만 연결할 수 있습니다. 서비스의 다른 리소스에 대한 액세스는 차단됩니다. 이 메커니즘은 데이터 유출 위험을 방지합니다.
- Global Reach: 다른 지역에서 실행되는 서비스에 비공개로 연결합니다. 소비자의 가상 네트워크는 A 지역에 있으며, B 지역의 Private Link 뒤에 있는 서비스에 연결할 수 있습니다.
- 사용자 고유의 서비스로 확장: 동일한 환경과 기능을 사용하여 자체 서비스를 Azure의 소비자에게 비공개로 렌더링할 수 있습니다. 서비스를 표준 Azure Load Balancer 뒤에 배치하여 Private Link에 사용할 수 있습니다. 그러면 소비자는 자체 가상 네트워크에서 프라이빗 엔드포인트를 사용하여 서비스에 직접 연결할 수 있습니다. 승인 호출 흐름을 사용하여 연결 요청을 관리할 수 있습니다. Azure Private Link는 다른 Microsoft Entra 테넌트에 속하는 소비자 및 서비스에 대해 작동합니다.
참고
Azure Virtual Network와 함께 Azure Private Link는 Azure 가용성 영역에 걸쳐 있으므로 영역 복원력이 있습니다. 프라이빗 엔드포인트를 사용하여 Azure 리소스에 고가용성을 제공하려면 리소스가 영역 복원력이 있는지 확인합니다.
가용성
Private Link를 지원하는 Azure 서비스에 대한 자세한 내용은 Azure Private Link 가용성을 참조하세요.
최신 알림은 Azure Private Link 업데이트 페이지를 확인하세요.
로깅 및 모니터링
Azure Private Link는 Azure Monitor와 통합되었습니다. 이 조합을 통해 다음을 수행할 수 있습니다.
- 스토리지 계정에 로그를 보관합니다.
- 이벤트를 Event Hubs로 스트리밍합니다.
- Azure Monitor 로깅이 가능합니다.
Azure Monitor에서 다음 정보에 액세스할 수 있습니다.
- 프라이빗 엔드포인트:
- 프라이빗 엔드포인트에서 처리한 데이터(수신/송신)
- Private Link 서비스:
- Private Link 서비스에서 처리한 데이터(수신/송신)
- NAT 포트 가용성
가격 책정
가격 책정에 대한 자세한 내용은 Azure Private Link 가격 책정을 참조하세요.
FAQ
FAQ는 Azure Private Link FAQ를 참조하세요.
제한
제한은 Azure Private Link 제한을 참조하세요.
서비스 수준 계약
SLA는 Azure Private Link에 대한 SLA를 참조하세요.
'IT이야기 > Azure' 카테고리의 다른 글
| Azure DNS Private Resolver (0) | 2024.10.18 |
|---|---|
| 애플리케이션 보안 그룹 (0) | 2024.10.18 |
| 네트워크 보안 그룹 (0) | 2024.10.18 |
| 가상 네트워크 서비스 태그 (0) | 2024.10.18 |
| Azure VM에 중첩 가상화 구성하기 (0) | 2024.07.18 |